PostgreSQL Source (JDBC) Connector for Confluent Cloud¶
The fully-managed PostgreSQL Source connector for Confluent Cloud can obtain a snapshot of the existing data in a PostgreSQL database and then monitor and record all subsequent row-level changes to that data. The connector supports Avro, JSON Schema, Protobuf, or JSON (schemaless) output data formats. All of the events for each table are recorded in a separate Apache Kafka® topic. The events can then be easily consumed by applications and services. Note that deleted records are not captured.
Note
- This Quick Start is for the fully-managed Confluent Cloud connector. If you are installing the connector locally for Confluent Platform, see JDBC Connector (Source and Sink) for Confluent Platform.
- If you require private networking for fully-managed connectors, make sure to set up the proper networking beforehand. For more information, see Manage Networking for Confluent Cloud Connectors.
Features¶
The PostgreSQL Source connector provides the following features:
Topics created automatically: The connector automatically creates Kafka topics using the naming convention:
<topic.prefix><tableName>. The tables are created with the properties:topic.creation.default.partitions=1andtopic.creation.default.replication.factor=3.Insert modes:
timestamp mode is enabled when only a timestamp column is specified when you enter database details.
timestamp+incrementing mode is enabled when both a timestamp column and incrementing column are specified when you enter database details.
Important
A timestamp column must not be nullable.
Database authentication: Uses password authentication.
SSL Support: Supports one-way SSL.
Data Format with or without a Schema: The connector supports Avro, JSON Schema, Protobuf, JSON (schemaless), or Bytes. Schema Registry must be enabled to use a Schema Registry-based format (for example, Avro, JSON_SR (JSON Schema), or Protobuf). See Schema Registry Enabled Environments for additional information.
Select configuration properties:
db.timezonepoll.interval.msbatch.max.rowstimestamp.delay.interval.mstopic.prefixschema.pattern
PostgreSQL JSON and JSONB: The connector supports sourcing from PostgreSQL tables containing data stored as JSON or JSONB (JSON binary format). The connector stores JSON or JSONB as STRING type in Kafka.
Offset management capabilities: Supports offset management. For more information, see Manage custom offsets.
For more information and examples to use with the Confluent Cloud API for Connect, see the Confluent Cloud API for Connect Usage Examples section.
Limitations¶
Be sure to review the following information.
- For connector limitations, see PostgreSQL Source (JDBC) Connector limitations.
- If you plan to use one or more Single Message Transforms (SMTs), see SMT Limitations.
- If you plan to use Confluent Cloud Schema Registry, see Schema Registry Enabled Environments.
Note
CockroachDB is not supported.
Manage custom offsets¶
You can manage the offsets for this connector. Offsets provide information on the point in the system from which the connector is accessing data. For more information, see Manage Offsets for Fully-Managed Connectors in Confluent Cloud.
To manage offsets:
- Manage offsets using Confluent Cloud APIs. For more information, see Cluster API reference.
To get the current offset, make a GET request that specifies the environment, Kafka cluster, and connector name.
GET /connect/v1/environments/{environment_id}/clusters/{kafka_cluster_id}/connectors/{connector_name}/offsets
Host: https://api.confluent.cloud
Response:
Successful calls return HTTP 200 with a JSON payload that describes the offset.
{
"id": "lcc-example123",
"name": "{connector_name}",
"offsets": [
{
"partition": {
"protocol": "1",
"table": "{table_name}"
},
"offset": {
"incrementing": 26
}
}
],
"metadata": {
"observed_at": "2024-03-28T17:57:48.139635200Z"
}
}
Responses include the following information:
- The position of latest offset.
- The observed time of the offset in the metadata portion of the payload. The
observed_attime indicates a snapshot in time for when the API retrieved the offset. A running connector is always updating its offsets. Useobserved_atto get a sense for the gap between real time and the time at which the request was made. By default, offsets are observed every minute. CallingGETrepeatedly will fetch more recently observed offsets. - Information about the connector.
- In these examples, the curly braces around “{connector_name}” indicate a replaceable value.
To update the offset, make a POST request that specifies the environment, Kafka cluster, and connector
name. Include a JSON payload that specifies new offset and a patch type.
POST /connect/v1/environments/{environment_id}/clusters/{kafka_cluster_id}/connectors/{connector_name}/offsets/request
Host: https://api.confluent.cloud
{
"type": "PATCH",
"offsets": [
{
"partition": {
"protocol": "1",
"table": "{table_name}"
},
"offset": {
"incrementing": 3
}
}
]
}
Considerations:
- You can only make one offset change at a time for a given connector.
- This is an asynchronous request. To check the status of this request, you must use the check offset status API. For more information, see Get the status of an offset request.
- For source connectors, the connector attempts to read from the position defined by the requested offsets.
Response:
Successful calls return HTTP 202 Accepted with a JSON payload that describes the offset.
{
"id": "lcc-example123",
"name": "{connector_name}",
"offsets": [
{
"partition": {
"protocol": "1",
"table": "{table_name}"
},
"offset": {
"incrementing": 3
}
}
],
"requested_at": "2024-03-28T17:58:45.606796307Z",
"type": "PATCH"
}
Responses include the following information:
- The requested position of the offsets in the source.
- The time of the request to update the offset.
- Information about the connector.
To delete the offset, make a POST request that specifies the environment, Kafka cluster, and connector
name. Include a JSON payload that specifies the delete type.
POST /connect/v1/environments/{environment_id}/clusters/{kafka_cluster_id}/connectors/{connector_name}/offsets/request
Host: https://api.confluent.cloud
{
"type": "DELETE"
}
Considerations:
- Delete requests delete the offset for the provided partition and reset to the base state. A delete request is as if you created a fresh new connector.
- This is an asynchronous request. To check the status of this request, you must use the check offset status API. For more information, see Get the status of an offset request.
- Do not issue delete and patch requests at the same time.
- For source connectors, the connector attempts to read from the position defined in the base state.
Response:
Successful calls return HTTP 202 Accepted with a JSON payload that describes the result.
{
"id": "lcc-example123",
"name": "{connector_name}",
"offsets": [],
"requested_at": "2024-03-28T17:59:45.606796307Z",
"type": "DELETE"
}
Responses include the following information:
- Empty offsets.
- The time of the request to delete the offset.
- Information about Kafka cluster and connector.
- The type of request.
To get the status of a previous offset request, make a GET request that specifies the environment, Kafka cluster, and connector
name.
GET /connect/v1/environments/{environment_id}/clusters/{kafka_cluster_id}/connectors/{connector_name}/offsets/request/status
Host: https://api.confluent.cloud
Considerations:
- The status endpoint always shows the status of the most recent PATCH/DELETE operation.
Response:
Successful calls return HTTP 200 with a JSON payload that describes the result. The following is an example
of an applied patch.
{
"request": {
"id": "lcc-example123",
"name": "{connector_name}",
"offsets": [
{
"partition": {
"protocol": "1",
"table": "{table_name}"
},
"offset": {
"incrementing": 3
}
}
],
"requested_at": "2024-03-28T17:58:45.606796307Z",
"type": "PATCH"
},
"status": {
"phase": "APPLIED",
"message": "The Connect framework-managed offsets for this connector have been altered successfully. However, if this connector manages offsets externally, they will need to be manually altered in the system that the connector uses."
},
"previous_offsets": [
{
"partition": {
"protocol": "1",
"table": "{table_name}"
},
"offset": {
"incrementing": 26
}
}
],
"applied_at": "2024-03-28T17:58:48.079141883Z"
}
Responses include the following information:
- The original request, including the time it was made.
- The status of the request: applied, pending, or failed.
- The time you issued the status request.
- The previous offsets. These are the offsets that the connector last updated prior to updating the offsets. Use these to try to restore the state of your connector if a patch update causes your connector to fail or to return a connector to its previous state after rolling back.
JDBC modes and offsets¶
You can run the JDBC source connectors in one of four modes. Each mode uses a different offset object in its JSON payload to track the progress of the connector. The provided samples show an offset object from a JBDC source connector in incrementing mode.
bulk- No offset. This is the default mode for JDBC source connectors.incrementing- The offset is provided by theincrementingproperty in the offset object.timestamp- The offset is provided by thetimestampandtimestamp-nanosproperties in the offset object.timestamp+incrementing- The offset is provided by theincrementing,timestampandtimestamp-nanosproperties in the offset object.
JSON payload¶
The table below offers a description of the unique fields in the JSON payload for managing offsets of the JDBC Source connectors, including:
- Microsoft SQL Server Source connector
- MySQL Source connector
- Oracle Database Source connector
- PostgreSQL Source connector
| Field | Definition | Required/Optional |
|---|---|---|
incrementing |
Specifies the value of Available only in the following modes: incrementing, timestamp+incrementing. |
Required |
protocol |
Specifies the protocol. Available in the following modes: incrementing, timestamp, timestamp+incrementing. |
Required |
table |
The name of the table. Available in the following modes: incrementing, timestamp, timestamp+incrementing. |
Required |
timestamp |
The number of milliseconds since Available only in the following modes: timestamp, timestamp+incrementing. |
Required |
timestamp_nanos |
Fractional seconds component of the timestamp object. Available only in the following modes: timestamp, timestamp+incrementing. |
Required |
Quick Start¶
Use this quick start to get up and running with the Confluent Cloud PostgreSQL Source connector. The quick start provides the basics of selecting the connector and configuring it to obtain a snapshot of the existing data in a PostgreSQL database and then monitoring and recording all subsequent row-level changes.
- Prerequisites
Authorized access to a Confluent Cloud cluster on Amazon Web Services (AWS), Microsoft Azure (Azure), or Google Cloud.
The Confluent CLI installed and configured for the cluster. See Install the Confluent CLI.
The connector automatically creates Kafka topics using the naming convention:
<topic.prefix><tableName>. The tables are created with the properties:topic.creation.default.partitions=1andtopic.creation.default.replication.factor=3. If you want to create topics with specific settings, create the topics before running this connector.Important
If you are configuring granular access using a service account, and you leave the optional Topic prefix (
topic.prefix) configuration property empty, you must grant ACLCREATEandWRITEaccess to all the Kafka topics or create RBAC role bindings. To add ACLs, you use the (*) wildcard in the ACL entries as shown in the following examples.confluent kafka acl create --allow --service-account "<service-account-id>" --operation create --topic "*"
confluent kafka acl create --allow --service-account "<service-account-id>" --operation write --topic "*"
Schema Registry must be enabled to use a Schema Registry-based format (for example, Avro, JSON_SR (JSON Schema), or Protobuf). See Schema Registry Enabled Environments for additional information.
You cannot use a basic database with Azure. You must use a general purpose or memory-optimized PostgreSQL database.
Make sure your connector can reach your service. Consider the following before running the connector:
- Depending on the service environment, certain network access limitations may exist. See Manage Networking for Confluent Cloud Connectors for details.
- To use a set of public egress IP addresses, see Public Egress IP Addresses for Confluent Cloud Connectors. For additional fully-managed connector networking details, see Networking and DNS.
- Do not include
jdbc:xxxx://in the connection hostname property. An example of a connection hostname property isdatabase.example.endpoint.com. For example,mydatabase.abc123ecs2.us-west.rds.amazonaws.com. - Clients from Azure Virtual Networks are not allowed to access the server by default. Check that your Azure Virtual Network is correctly configured and that Allow access to Azure Services is enabled.
- See your specific cloud platform documentation for how to configure security rules for your VPC.
- Kafka cluster credentials. The following lists the different ways you can provide credentials.
- Enter an existing service account resource ID.
- Create a Confluent Cloud service account for the connector. Make sure to review the ACL entries required in the service account documentation. Some connectors have specific ACL requirements.
- Create a Confluent Cloud API key and secret. To create a key and secret, you can use confluent api-key create or you can autogenerate the API key and secret directly in the Cloud Console when setting up the connector.
Using the Confluent Cloud Console¶
Step 1: Launch your Confluent Cloud cluster¶
See the Quick Start for Confluent Cloud for installation instructions.
Step 2: Add a connector¶
In the left navigation menu, click Connectors. If you already have connectors in your cluster, click + Add connector.
Step 4: Enter the connector details¶
Note
- Make sure you have all your prerequisites completed.
- An asterisk ( * ) designates a required entry.
At the Postgres Source Connector screen, complete the following:
In the Topic prefix field, define a topic prefix your connector will
use to publish to Kafka topics. The connector will Kafka topics using the
following naming convention: <topic.prefix><tableName>.
Important
If you are configuring granular access using a service account, and you leave the optional Topic prefix
(topic.prefix) configuration property empty, you must grant ACL
CREATE and WRITE access to all the Kafka topics or create RBAC
role bindings. To add ACLs, you use the (*)
wildcard in the ACL entries as shown in the following examples.
confluent kafka acl create --allow --service-account
"<service-account-id>" --operation create --topic "*"
confluent kafka acl create --allow --service-account
"<service-account-id>" --operation write --topic "*"
- Select the way you want to provide Kafka Cluster credentials. You can
choose one of the following options:
- My account: This setting allows your connector to globally access everything that you have access to. With a user account, the connector uses an API key and secret to access the Kafka cluster. This option is not recommended for production.
- Service account: This setting limits the access for your connector by using a service account. This option is recommended for production.
- Use an existing API key: This setting allows you to specify an API key and a secret pair. You can use an existing pair or create a new one. This method is not recommended for production environments.
Note
Freight clusters support only service accounts for Kafka authentication.
- Click Continue.
- Add the following database connection details:
- Connection host: The JDBC connection host. Do not include
jdbc:xxxx://in the connection hostname property. An example of a connection hostname property isdatabase-1.123abc456ecs2.us-west-2.rds.amazonaws.com. Depending on the service environment, certain network access limitations may exist. For details, see Manage Networking for Confluent Cloud Connectors. - Connection port: JDBC connection port for PostgreSQL.
- Connection user: JDBC connection user for PostgreSQL.
- Connection password: JDBC connection password for PostgreSQL.
- Database name: JDBC database name for PostgreSQL.
- SSL mode: The SSL mode to use to connect to your database.
- SSL root cert: The server root certification file used for
certificate validation. Only required if using
verify-caorverify-fullSSL mode.
- Connection host: The JDBC connection host. Do not include
- Click Continue.
Configure the following:
- Table names: List of tables to include in copying. Use a
comma-separated list to specify multiple tables (for example,
User, Address, Email). - Select the output record value format (data going to the Kafka topic): AVRO, JSON, JSON_SR (JSON Schema), or PROTOBUF. Schema Registry must be enabled to use a Schema Registry-based format (for example, Avro, JSON Schema, or Protobuf). For additional information, see Schema Registry Enabled Environments.
- Table types: By default, the JDBC connector will only detect
tables with type
TABLEfrom the source database. This config allows a command separated list of table types to extract. - Database timezone: Name of the JDBC timezone used in the
connector when querying with time-based criteria. Defaults to
UTC.
Show advanced configurations
Schema context: Select a schema context to use for this connector, if using a schema-based data format. This property defaults to the Default context, which configures the connector to use the default schema set up for Schema Registry in your Confluent Cloud environment. A schema context allows you to use separate schemas (like schema sub-registries) tied to topics in different Kafka clusters that share the same Schema Registry environment. For example, if you select a non-default context, a Source connector uses only that schema context to register a schema and a Sink connector uses only that schema context to read from. For more information about setting up a schema context, see What are schema contexts and when should you use them?.
Mode: The mode for updating a table each time it is polled. Defaults to
bulkmode.Quote SQL Identifiers: When to quote table names, column names, and other identifiers in SQL statements. For backward compatibility, the default value is
ALWAYS.Transaction Isolation Level: Isolation level determines how transaction integrity is visible to other users and systems.
DEFAULTis the default isolation level configured at the database server.READ_UNCOMMITTEDis the lowest isolation level. At this level, a transaction may see changes that are not committed (that is, dirty reads) made by other transactions.READ_COMMITTEDguarantees that any data read is already committed at the moment it is read.REPEATABLE_READadds to the guarantees of theREAD_COMMITTEDlevel with the addition of also guaranteeing that any data read cannot change, if the transaction reads the same data again. However, phantom reads are possible.SERIALIZABLEis the highest isolation level. In addition to everythingREPEATABLE_READguarantees,SERIALIZABLEalso eliminates phantom reads.Numeric Mapping: Map NUMERIC values by precision and optionally scale to integral or decimal types.
Initial timestamp: The epoch timestamp used for initial queries that use timestamp criteria. The value -1 sets the initial timestamp to the current time. If not specified, the connector retrieves all data. Once the connector has managed to successfully record a source offset, this property has no effect even if changed to a different value later on.
Timestamp column name: Comma-separated list of one or more timestamp columns to detect new or modified rows using the COALESCE SQL function. Rows whose first non-null timestamp value is greater than the largest previous timestamp value seen will be discovered with each poll. At least one column should not be nullable.
Incrementing column name: The name of the strictly incrementing column to use to detect new rows. Any empty value indicates the column should be autodetected by looking for an auto-incrementing column. This column may not be nullable.
Schema pattern: Schema pattern to fetch table metadata from the database.
Timestamp granularity for timestamp columns: Defines the granularity of the Timestamp column.
CONNECT_LOGICAL(default) represents timestamp values using Connect’s built-in representations.NANOS_LONGrepresents timestamp values as nanoseconds (ns) since the epoch (UNIX epoch time).NANOS_STRINGrepresents timestamp values as ns since the epoch in string format.NANOS_ISO_DATETIME_STRINGrepresents timestamp values in ISO formatyyyy-MM-dd'T'HH:mm:ss.n.Poll interval (ms): Enter the number of milliseconds (ms) the connector should wait during each iteration for new change events to appear. Defaults to
1000ms (1 second).Max rows per batch: Specify how the connector reacts to exceptions when processing binlog events. Defaults to
fail. Selectskiporwarnto skip the event or issue a warning, respectively.Delay interval (ms): Specify how binary (blob, binary) columns are represented in change events. Select
bytes(the default) to represent binary data in byte array format. Selectbase64to represent binary data in base64-encoded string format. Selecthexto represent binary data in hex-encoded (base16) string format.Transforms and Predicates: For details, see the Single Message Transforms (SMT) documentation.
For all property values and definitions, see Configuration Properties.
- Table names: List of tables to include in copying. Use a
comma-separated list to specify multiple tables (for example,
Click Continue.
Based on the number of topic partitions you select, you will be provided with a recommended number of tasks.
- To change the number of tasks, use the Range Slider to select the desired number of tasks.
- Click Continue.
Verify the connection details by previewing the running configuration.
Tip
For information about previewing your connector output, see Data Previews for Confluent Cloud Connectors.
After you’ve validated that the properties are configured to your satisfaction, click Launch.
The status for the connector should go from Provisioning to Running.
Step 5: Check the Kafka topic¶
After the connector is running, verify that messages are populating your Kafka topic.
For more information and examples to use with the Confluent Cloud API for Connect, see the Confluent Cloud API for Connect Usage Examples section.
Using the Confluent CLI¶
Complete the following steps to set up and run the connector using the Confluent CLI.
Note
Make sure you have all your prerequisites completed.
Step 1: List the available connectors¶
Enter the following command to list available connectors:
confluent connect plugin list
Step 2: List the connector configuration properties¶
Enter the following command to show the connector configuration properties:
confluent connect plugin describe <connector-plugin-name>
The command output shows the required and optional configuration properties.
Step 3: Create the connector configuration file¶
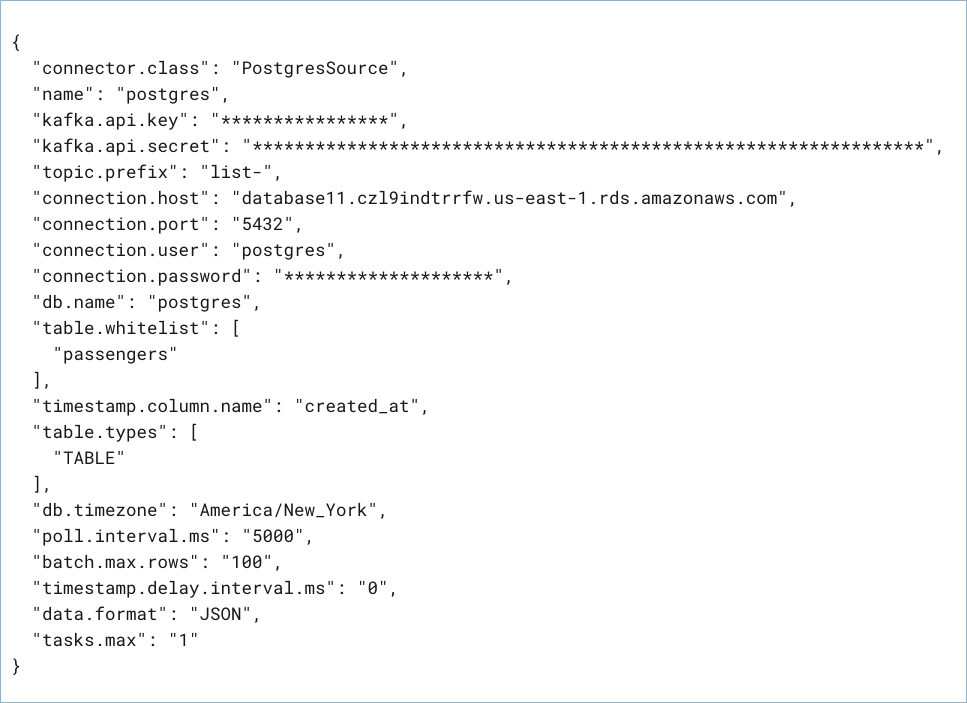
Create a JSON file that contains the connector configuration properties. The following example shows the required connector properties.
{
"name" : "confluent-postgresql-source",
"connector.class": "PostgresSource",
"kafka.api.key": "<my-kafka-api-key>",
"kafka.auth.mode": "KAFKA_API_KEY",
"kafka.api.secret" : "<my-kafka-api-secret>",
"topic.prefix" : "postgresql_",
"ssl.mode" : "prefer",
"connection.host" : "<my-database-endpoint>",
"connection.port" : "5432",
"connection.user" : "postgres",
"connection.password": "<my-database-password>",
"db.name": "postgres",
"table.whitelist": "passengers",
"timestamp.column.name": "created_at",
"output.data.format": "JSON",
"db.timezone": "UTC",
"tasks.max" : "1"
}
Note the following property definitions:
"name": Sets a name for your new connector."connector.class": Identifies the connector plugin name.
"kafka.auth.mode": Identifies the connector authentication mode you want to use. There are two options:SERVICE_ACCOUNTorKAFKA_API_KEY(the default). To use an API key and secret, specify the configuration propertieskafka.api.keyandkafka.api.secret, as shown in the example configuration (above). To use a service account, specify the Resource ID in the propertykafka.service.account.id=<service-account-resource-ID>. To list the available service account resource IDs, use the following command:confluent iam service-account list
For example:
confluent iam service-account list Id | Resource ID | Name | Description +---------+-------------+-------------------+------------------- 123456 | sa-l1r23m | sa-1 | Service account 1 789101 | sa-l4d56p | sa-2 | Service account 2
"topic.prefix": Enter a topic prefix. The connector automatically creates Kafka topics using the naming convention:<topic.prefix><tableName>. The tables are created with the properties:topic.creation.default.partitions=1andtopic.creation.default.replication.factor=3. If you want to create topics with specific settings, create the topics before running this connector. If you are configuring granular access using a service account, you must set up ACLs for the topic prefix.Important
If you are configuring granular access using a service account, and you leave the optional Topic prefix (
topic.prefix) configuration property empty, you must grant ACLCREATEandWRITEaccess to all the Kafka topics or create RBAC role bindings. To add ACLs, you use the (*) wildcard in the ACL entries as shown in the following examples.confluent kafka acl create --allow --service-account "<service-account-id>" --operation create --topic "*"
confluent kafka acl create --allow --service-account "<service-account-id>" --operation write --topic "*"
The following provides more information about how to use the
ssl.modeproperty:- The default option
preferis enabled ifssl.modeis not added to the connector configuration. Whenpreferis enabled, the connector attempts to use an encrypted connection to the PostgreSQL server. preferandrequire: use a secure (encrypted) connection. The connector fails if a secure connection cannot be established. These modes do not do Certification Authority (CA) validation.verify-ca: similar torequire, but also verifies the server TLS certificate against the configured Certificate Authority (CA) certificates. Fails if no valid matching CA certificates are found.verify-full: similar toverify-ca, but also verifies that the server certificate matches the host to which the connection is attempted.
If you choose
verify-caorverify-full, use the propertyssl.rootcertfileand add the contents of the text certificate file for the property value. For example,"ssl.rootcertfile": "<certificate-text>".- The default option
The following provides more information about how to use the
timestamp.column.nameand``incrementing.column.name`` properties.- Enter a
timestamp.column.nameto enable timestamp mode. This mode uses a timestamp (or timestamp-like) column to detect new and modified rows. This assumes the column is updated with each write, and that values are monotonically incrementing, but not necessarily unique. - Enter both a
timestamp.column.nameand anincrementing.column.nameto enable timestamp+incrementing mode. This mode uses two columns, a timestamp column that detects new and modified rows, and a strictly incrementing column which provides a globally unique ID for updates so each row can be assigned a unique stream offset. By default, the connector only detectstable.typeswith typeTABLEfrom the source database. EnterVIEWfor virtual tables created from joining one or more tables. EnterALIASfor tables with a shortened or temporary name.
- Enter a
If you define a schema pattern in your database, you need to enter the
schema.patternproperty to fetch table metadata from the database.""retrieves table metadata for tables not using a schema.null(default) indicates that the schema name is not used to narrow the search and that all table metadata is fetched, regardless of the schema."output.data.format": Sets the output Kafka record value format (data coming from the connector). Valid entries are AVRO, JSON_SR, PROTOBUF, or JSON. You must have Confluent Cloud Schema Registry configured if using a schema-based message format (for example, Avro, JSON_SR (JSON Schema), or Protobuf)."db.timezone": Identifies the database timezone. This can be any valid database timezone. The default is UTC. For more information, see this list of database timezones.
Single Message Transforms: See the Single Message Transforms (SMT) documentation for details about adding SMTs using the CLI.
See Configuration Properties for all property values and definitions.
Step 4: Load the properties file and create the connector¶
Enter the following command to load the configuration and start the connector:
confluent connect cluster create --config-file <file-name>.json
For example:
confluent connect cluster create --config-file postgres-source.json
Example output:
Created connector confluent-postgresql-source lcc-ix4dl
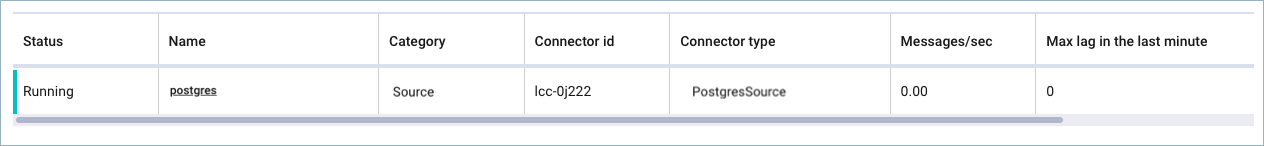
Step 5: Check the connector status¶
Enter the following command to check the connector status:
confluent connect cluster list
Example output:
ID | Name | Status | Type
+-----------+-----------------------------+---------+-------+
lcc-ix4dl | confluent-postgresql-source | RUNNING | source
Step 6: Check the Kafka topic.¶
After the connector is running, verify that messages are populating your Kafka topic.
For more information and examples to use with the Confluent Cloud API for Connect, see the Confluent Cloud API for Connect Usage Examples section.
Configuration Properties¶
Use the following configuration properties with the fully-managed connector. For self-managed connector property definitions and other details, see the connector docs in Self-managed connectors for Confluent Platform.
How should we connect to your data?¶
nameSets a name for your connector.
- Type: string
- Valid Values: A string at most 64 characters long
- Importance: high
Kafka Cluster credentials¶
kafka.auth.modeKafka Authentication mode. It can be one of KAFKA_API_KEY or SERVICE_ACCOUNT. It defaults to KAFKA_API_KEY mode.
- Type: string
- Default: KAFKA_API_KEY
- Valid Values: KAFKA_API_KEY, SERVICE_ACCOUNT
- Importance: high
kafka.api.keyKafka API Key. Required when kafka.auth.mode==KAFKA_API_KEY.
- Type: password
- Importance: high
kafka.service.account.idThe Service Account that will be used to generate the API keys to communicate with Kafka Cluster.
- Type: string
- Importance: high
kafka.api.secretSecret associated with Kafka API key. Required when kafka.auth.mode==KAFKA_API_KEY.
- Type: password
- Importance: high
Schema Config¶
schema.context.nameAdd a schema context name. A schema context represents an independent scope in Schema Registry. It is a separate sub-schema tied to topics in different Kafka clusters that share the same Schema Registry instance. If not used, the connector uses the default schema configured for Schema Registry in your Confluent Cloud environment.
- Type: string
- Default: default
- Importance: medium
How do you want to prefix table names?¶
topic.prefixPrefix to prepend to table names to generate the name of the Apache Kafka® topic to publish data to.
- Type: string
- Importance: high
How should we connect to your database?¶
connection.hostDepending on the service environment, certain network access limitations may exist. Make sure the connector can reach your service. Do not include jdbc:xxxx:// in the connection hostname property (e.g. database-1.abc234ec2.us-west.rds.amazonaws.com).
- Type: string
- Importance: high
connection.portJDBC connection port.
- Type: int
- Valid Values: [0,…,65535]
- Importance: high
connection.userJDBC connection user.
- Type: string
- Importance: high
connection.passwordJDBC connection password.
- Type: password
- Importance: high
db.nameJDBC database name.
- Type: string
- Importance: high
ssl.modeWhat SSL mode should we use to connect to your database. prefer and require allows for the connection to be encrypted but does not do certificate validation on the server. verify-ca and verify-full require a file containing SSL CA certificate to be provided. The server’s certificate will be verified to be signed by one of these authorities.`verify-ca` will verify that the server certificate is issued by a trusted CA. verify-full will verify that the server certificate is issued by a trusted CA and that the server hostname matches that in the certificate. Client authentication is not performed.
- Type: string
- Default: prefer
- Importance: high
ssl.rootcertfileThe server root cert file used for certificate validation. Only required if using verify-ca or verify-full ssl mode.
- Type: password
- Default: [hidden]
- Importance: low
Database details¶
table.whitelistList of tables to include in copying. Use a comma-separated list to specify multiple tables (for example: “User, Address, Email”).
- Type: list
- Importance: medium
timestamp.column.nameComma separated list of one or more timestamp columns to detect new or modified rows using the COALESCE SQL function. Rows whose first non-null timestamp value is greater than the largest previous timestamp value seen will be discovered with each poll. At least one column should not be nullable.
- Type: list
- Importance: medium
incrementing.column.nameThe name of the strictly incrementing column to use to detect new rows. Any empty value indicates the column should be autodetected by looking for an auto-incrementing column. This column may not be nullable.
- Type: string
- Default: “”
- Importance: medium
table.typesBy default, the JDBC connector will only detect tables with type TABLE from the source Database. This config allows a command separated list of table types to extract.
- Type: list
- Default: TABLE
- Importance: medium
schema.patternSchema pattern to fetch table metadata from the database.
- Type: string
- Importance: high
db.timezoneName of the JDBC timezone used in the connector when querying with time-based criteria. Defaults to UTC.
- Type: string
- Default: UTC
- Importance: medium
numeric.mappingMap NUMERIC values by precision and optionally scale to integral or decimal types. Use
noneif all NUMERIC columns are to be represented by Connect’s DECIMAL logical type. Usebest_fitif NUMERIC columns should be cast to Connect’s INT8, INT16, INT32, INT64, or FLOAT64 based upon the column’s precision and scale. Usebest_fit_eager_doubleif, in addition to the properties of best_fit described above, it is desirable to always cast NUMERIC columns with scale to Connect FLOAT64 type, despite potential of loss in accuracy. Useprecision_onlyto map NUMERIC columns based only on the column’s precision assuming that column’s scale is 0. Thenoneoption is the default, but may lead to serialization issues with Avro since Connect’s DECIMAL type is mapped to its binary representation, andbest_fitwill often be preferred since it maps to the most appropriate primitive type.- Type: string
- Default: none
- Importance: low
timestamp.granularityDefine the granularity of the Timestamp column. CONNECT_LOGICAL (default): represents timestamp values using Kafka Connect built-in representations. NANOS_LONG: represents timestamp values as nanos since epoch. NANOS_STRING: represents timestamp values as nanos since epoch in string. NANOS_ISO_DATETIME_STRING: uses iso format
- Type: string
- Default: CONNECT_LOGICAL
- Importance: low
Mode¶
modeThe mode for updating a table each time it is polled. BULK: perform a bulk load of the entire table each time it is polled. TIMESTAMP: use a timestamp (or timestamp-like) column to detect new and modified rows. This assumes the column is updated with each write, and that values are monotonically incrementing, but not necessarily unique. INCREMENTING: use a strictly incrementing column on each table to detect only new rows. Note that this will not detect modifications or deletions of existing rows. TIMESTAMP AND INCREMENTING: use two columns, a timestamp column that detects new and modified rows and a strictly incrementing column which provides a globally unique ID for updates so each row can be assigned a unique stream offset.
- Type: string
- Default: “”
- Importance: medium
quote.sql.identifiersWhen to quote table names, column names, and other identifiers in SQL statements. For backward compatibility, the default value is ALWAYS.
- Type: string
- Default: ALWAYS
- Valid Values: ALWAYS, NEVER
- Importance: medium
transaction.isolation.modeIsolation level determines how transaction integrity is visible to other users and systems. DEFAULT: This is the default isolation level configured at the Database Server. READ_UNCOMMITTED: This is the lowest isolation level. At this level, one transaction may see dirty reads (that is, not-yet-committed changes made by other transactions). READ_COMMITTED: This level guarantees that any data read is already committed at the moment it is read. REPEATABLE_READ: In addition to the guarantees of the READ_COMMITTED level, this option also guarantees that any data read cannot change, if the transaction reads the same data again. However, phantom reads are possible. SERIALIZABLE: This is the highest isolation level. In addition to everything REPEATABLE_READ guarantees, it also eliminates phantom reads.
- Type: string
- Default: DEFAULT
- Valid Values: DEFAULT, READ_COMMITTED, READ_UNCOMMITTED, REPEATABLE_READ, SERIALIZABLE
- Importance: medium
timestamp.initialThe epoch timestamp used for initial queries that use timestamp criteria. The value -1 sets the initial timestamp to the current time. If not specified, the connector retrieves all data. Once the connector has managed to successfully record a source offset, this property has no effect even if changed to a different value later on.
- Type: long
- Valid Values: [-1,…]
- Importance: medium
Connection details¶
poll.interval.msFrequency in ms to poll for new data in each table.
- Type: int
- Default: 5000 (5 seconds)
- Valid Values: [100,…]
- Importance: high
batch.max.rowsMaximum number of rows to include in a single batch when polling for new data. This setting can be used to limit the amount of data buffered internally in the connector.
- Type: int
- Default: 100
- Valid Values: [1,…,5000]
- Importance: low
timestamp.delay.interval.msHow long to wait after a row with a certain timestamp appears before we include it in the result. You may choose to add some delay to allow transactions with an earlier timestamp to complete. The first execution will fetch all available records (starting at timestamp 0) until current time minus the delay. Every following execution will get data from the last time we fetched until current time minus the delay.
- Type: int
- Default: 0
- Valid Values: [0,…]
- Importance: high
Output messages¶
output.data.formatSets the output Kafka record value format. Valid entries are AVRO, JSON_SR, PROTOBUF, or JSON. Note that you need to have Confluent Cloud Schema Registry configured if using a schema-based message format like AVRO, JSON_SR, and PROTOBUF
- Type: string
- Default: JSON
- Importance: high
schemas.enableInclude schemas within each of the serialized values.
- Type: boolean
- Default: false
- Importance: medium
replace.null.with.defaultWhether to replace fields that have a default value and that are null to the default value. When set to true, the default value is used, otherwise null is used.
- Type: boolean
- Default: true
- Importance: medium
ignore.default.for.nullablesWhen set to true, this property ensures that the corresponding record in Kafka is NULL, instead of showing the default column value.
- Type: boolean
- Default: false
- Importance: medium
Number of tasks for this connector¶
tasks.maxMaximum number of tasks for the connector.
- Type: int
- Valid Values: [1,…]
- Importance: high
Next Steps¶
For an example that shows fully-managed Confluent Cloud connectors in action with Confluent Cloud ksqlDB, see the Cloud ETL Demo. This example also shows how to use Confluent CLI to manage your resources in Confluent Cloud.